Authorization
Policy
A Policy defines what permissions a set of users or groups has. Policies are applied to Namespaces or Routes to associate the set of permissions with a service or set of service, completing the authentication model.
Policies can be constructed three ways:
Web UI
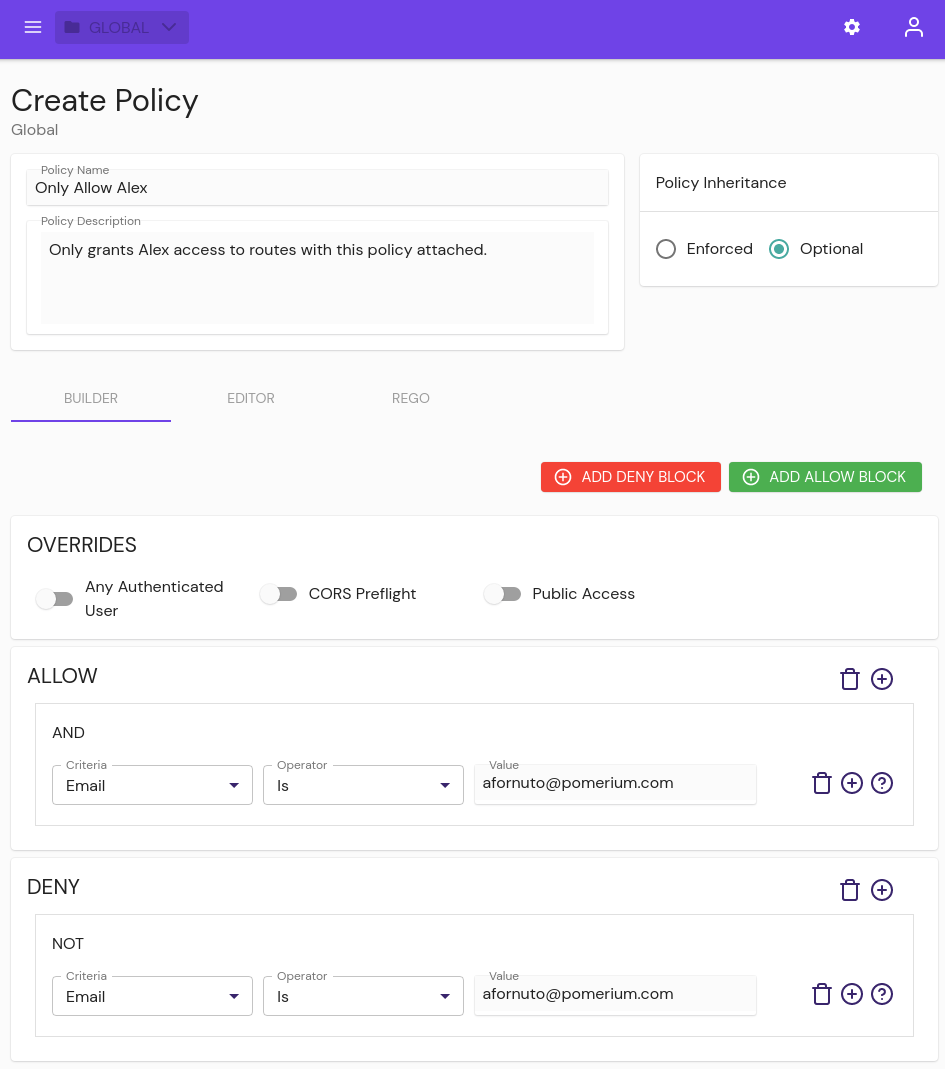
From the BUILDER tab, users can add allow or deny blocks to a policy, containing and/or/not/nor logic to allow or deny sets of users and groups.
Policies can be constructed three ways:
Pomerium Policy Language
From the EDITOR tab users can write policies in Pomerium Policy Language (PPL), a YAML-based notation.
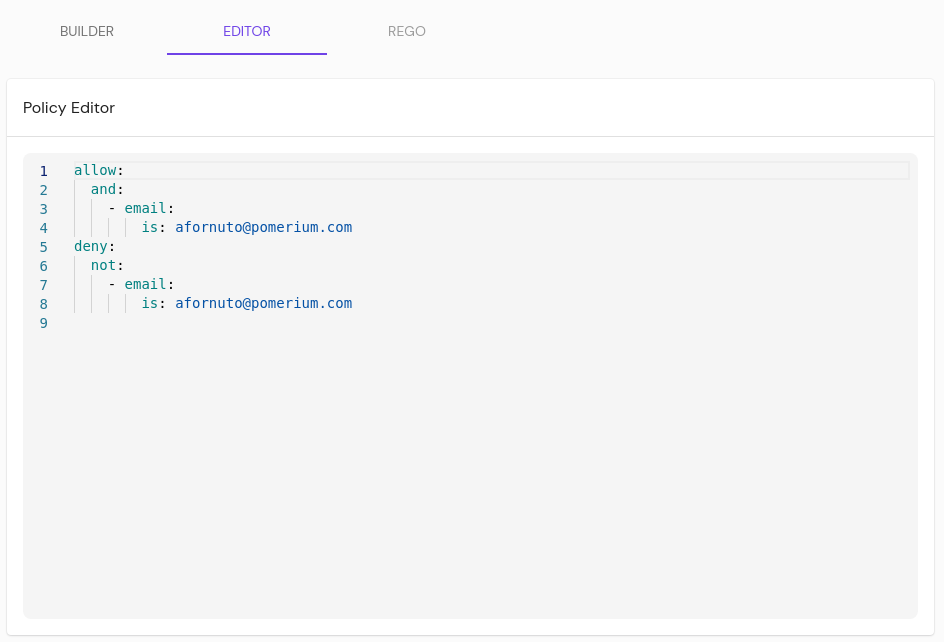
PPL documents contain one or more rules. Each rule has a corresponding action and one or more logical operators. Each logical operator contains criteria and each criterion has a name and corresponding data.
PPL documents are defined via YAML:
- allow:
or:
- email:
is: x@example.com
- email:
is: y@example.com
The available rule actions are:
allowdeny
The available logical operators are:
andornotnor
The available criteria types are:
acceptauthenticated_userclaimdateday_of_weekdomainemailgroupshttp_methodhttp_pathrecordrejecttime_of_dayuser
Some criteria also support a sub-path as part of the criterion name:
- allow:
or:
- claim/family_name: Smith
See Pomerium Policy Language for more details.
Rego
For those using OPA, the REGO tab will accept policies written in Rego.
A policy can only support PPL or Rego. Once one is set, the other tab is disabled.
Example Rego Policy
Overrides
- Any Authenticated User: This setting will allow access to a route with this policy attached to any user who can authenticate to your Identity Provider (IdP).
- CORS Preflight: Allow unauthenticated HTTP OPTIONS requests as per the CORS spec.
- Public Access: This setting allows complete, unrestricted access to an associated route. Use this setting with caution.
Devices
Introduced in v0.16.0, the Manage Devices page lets administrators manage user devices for policy-based authorization.
Manage Devices
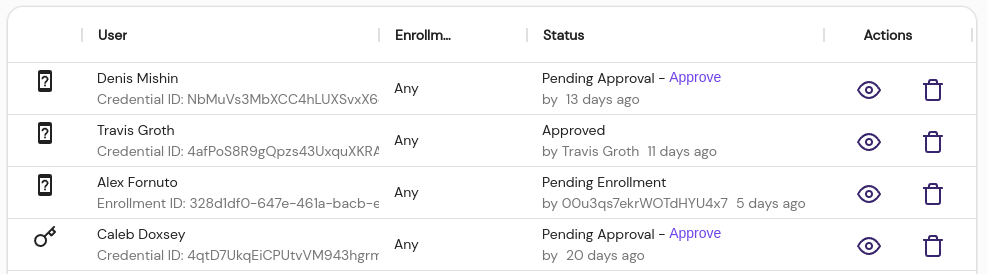
Devices List
Displays the currently enrolled devices for each user, along with their current approval status. Administrators can inspect, approve, or delete registered devices from this table.